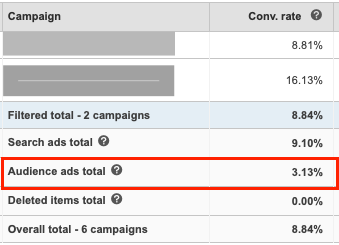
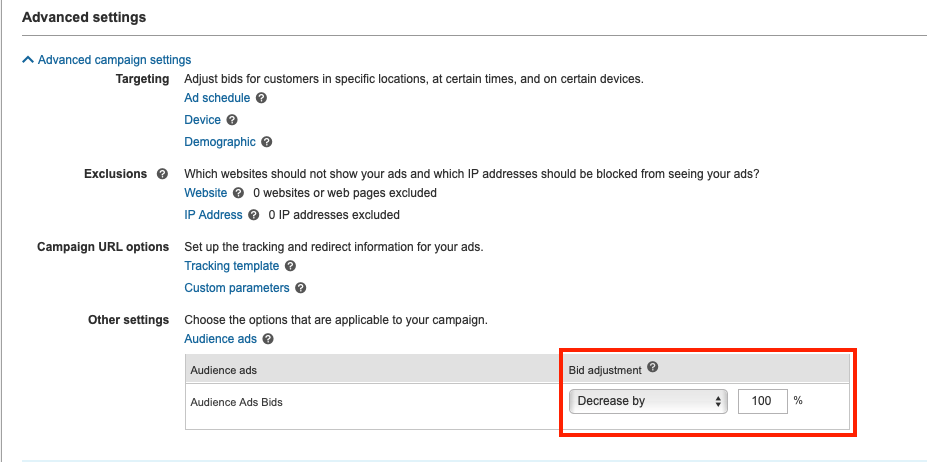
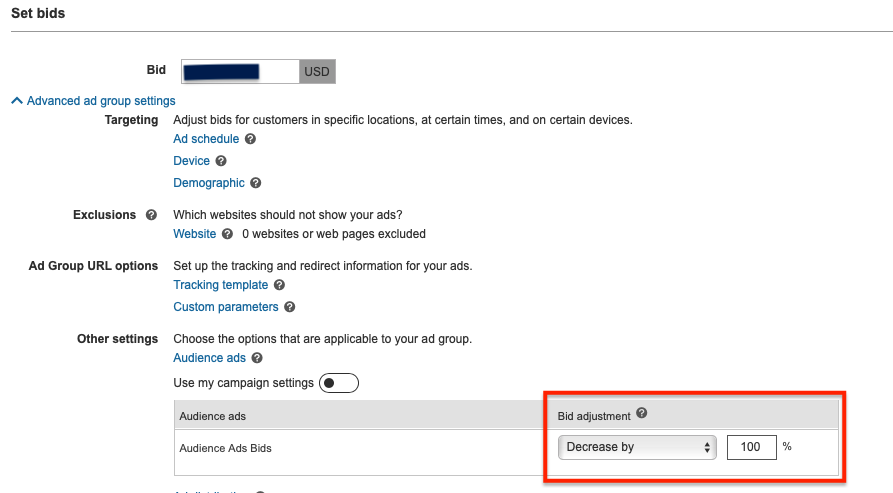
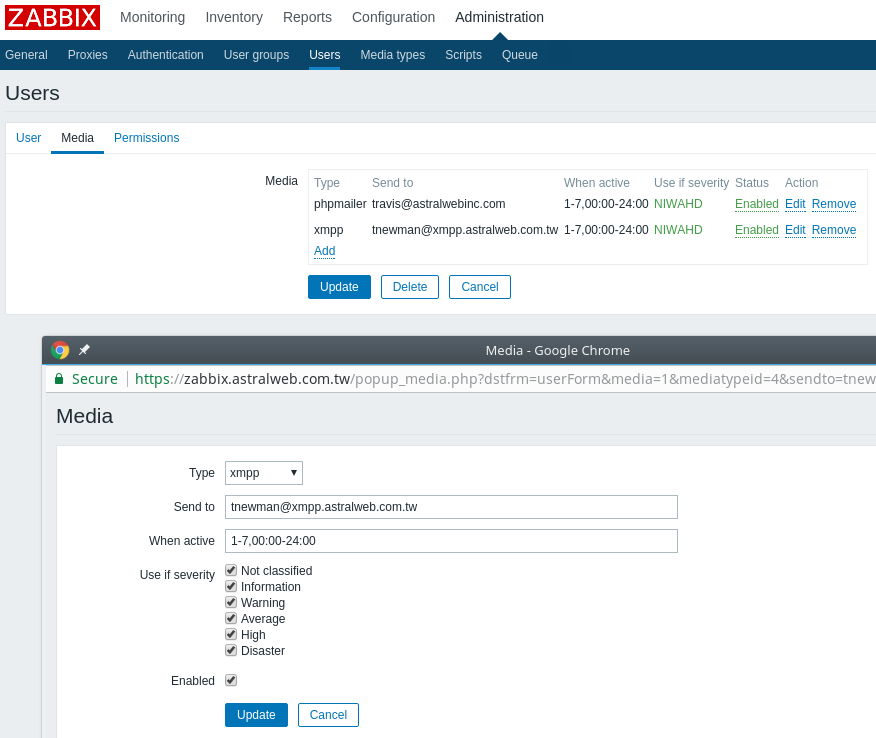
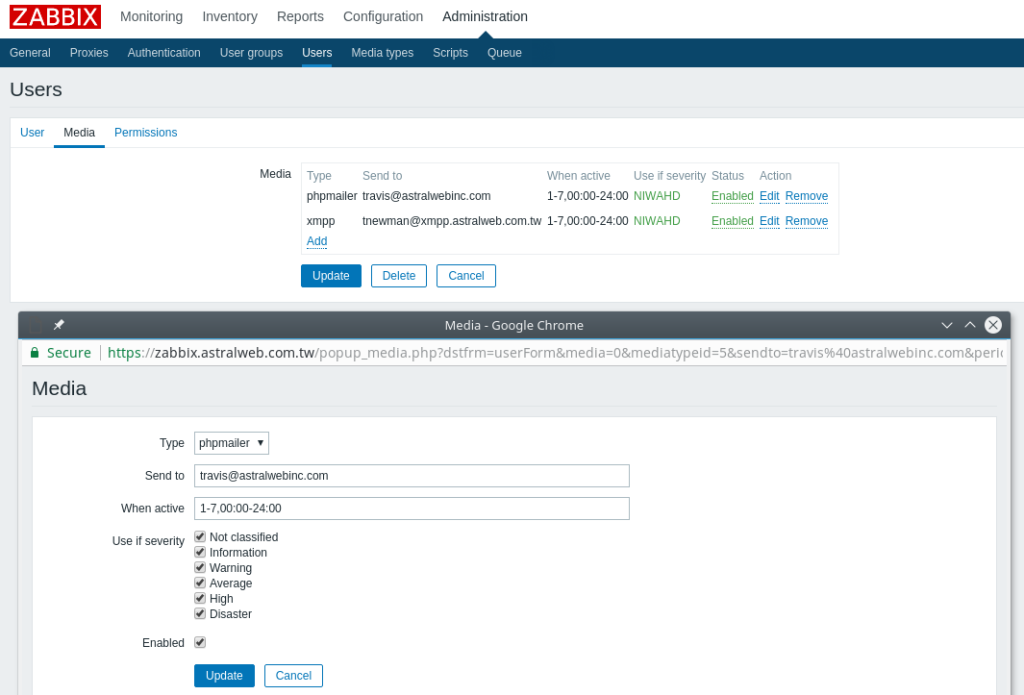
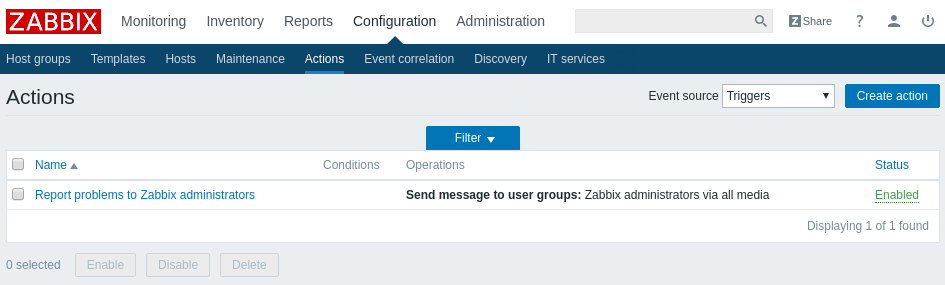
In 2020, Astral Web has released a range of apps for Shopify store owners to help grow online and extend shops with needed functionality.
We will continue to add new Shopify apps and listen to our customer requests.
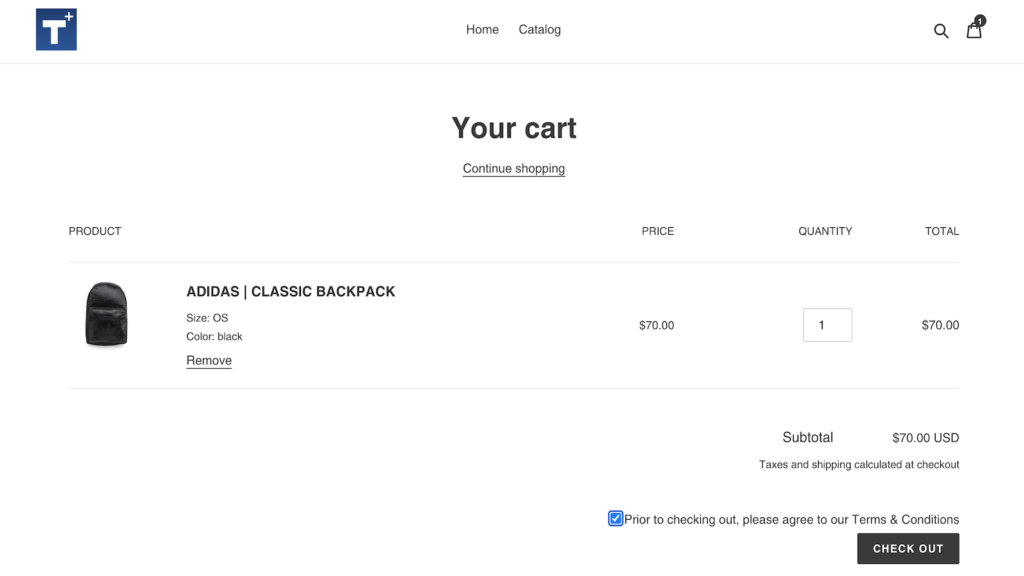
Require terms and conditions consent before customer checkout
Get maximum SEO value for your product images alt text tags

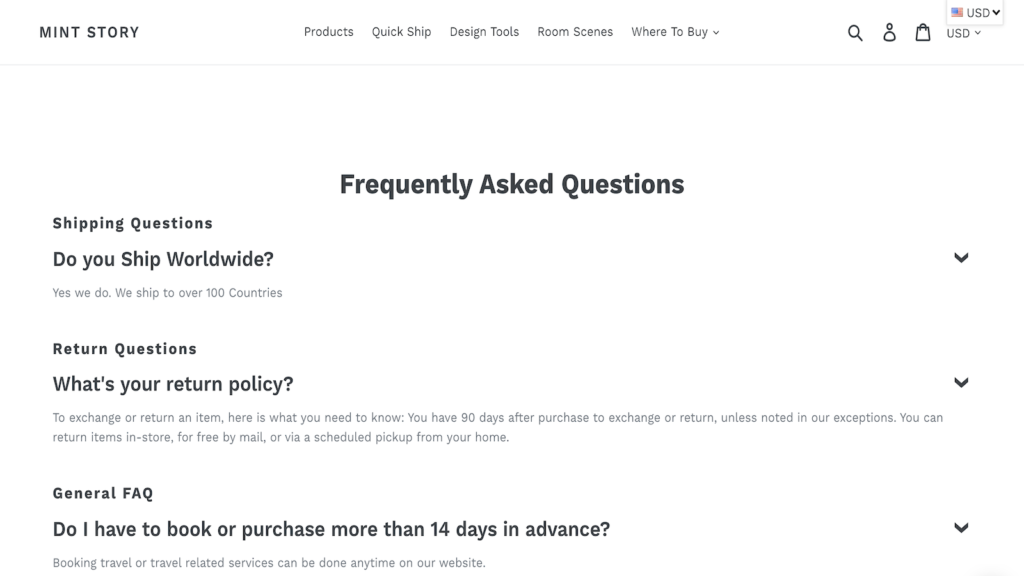
Easily create a great FAQ section for your store
Tools to guide customers with sticky bars to checkout